Introduction
Disclaimer: This is a personal blog. Any views or opinions represented in this blog are personal and belong solely to the blog owner and do not represent those of people, institutions or organizations that the owner may or may not be associated with in professional or personal capacity, unless explicitly stated.

I have spent the last 10 years of my career advocating VDI for a good number of reasons, some of which have drastically changed over time. From ease of management to centralized administration to enhanced security to remote digital work passing through a positive ROI, VDI as a concept had a lot to offer but the reality of the technology did not, until just recently. I will never trash VDI, its definitely not a “legacy” technology nor a “dead” end and has much more to offer than what we will discuss in a minute, and will never be a legacy concept as long as new delivery models such as DaaS adapt with new technologies such as cloud (VDI is a technology, DaaS is a delivery model).
VDI or otherwise, technology in business has a sole purpose of increasing user productivity or at least maintaining it else it has no value what so ever. Maybe in the distant future when robots take over this would be an obsolete statement but for now users are the center of productivity for any organization. As the day-to-day technology used by users evolved so did the workplace environment in order to stay relevant, cope and ultimately gain a competitive advantage. Productivity comes in all shapes and sizes so the metric to evaluate the same is highly contextual and subjective, yet organizations that have a digitally enabled workplace in general are clearly more productive and set to face complex situations and harsh circumstances.
Yes this is going to be a long post covering a technology that can be summarized in a few words but I want to take the time to put some context in-place before pitching a specific product so that you can understand where I am coming from. I do not do marketing nor do I do sales on my blog (hence the disclaimer), this is coming from a pure technology background and there are no hidden agendas in place noting that this my own personal perspective which is prone to error and maybe sentiment so caution is advised.
This might or might not fit your requirements so no generalized statements here, feel free to test the same as per the below instructions and assess if it adds value to your business, solves a problem facing your organization, and/or meets your requirements. Take advantage of the low resources requirements and 30 days free license to utilize the same at least in the current Coronavirus situation.
Pandemic Dilemma

In times of crisis specifically, such as the coronavirus pandemic, and even in our ever-evolving digitalized workplace generally, employees mostly prefer or are forced to work from their preferred location using their preferred devices under varying circumstances which are sometimes out of their control and probably ours. The remote digital workplace is no more a luxury for businesses but rather an absolute survival necessity. Organizations now have a legal, moral, and self-preservation obligation to provide users with all the required resources needed to conduct their day-to-day work in an efficient and timely manner remotely regardless of their location, device, and/or subjective situation.
That been said and regardless of varying circumstances however severe they may be, organizations still need to adhere to local and international regulations that being data security for example amongst many others and organizations still need to force their internal policies and procedures to maintain quality and value. Being able to do so, at least for many organizations that are yet to adopt technologies that enable a true remote digital workplace, is hard to achieve under normal circumstances let alone while working through a worldwide pandemic.
The equilibrium between user productivity and infrastructure security in any digitalized workplace is a fine example of how organizations need to provide users wherever they are, using whatever devices they have, and under whatever situation they are in, with all the tools necessary for them to conduct work while in the same time assuring the highest level of security and assurance of the organization’s data, users, applications, systems, and endpoints.
During a global crisis, organizations do not have time to acquire resources nor do they want to implement complex solutions, they simply want a secure way to facilitate remote access to resources needed by employees to conduct their work in an efficient manner from any location using any device while maintaining the levels of security dictated by the organization. The solution to facilitate the same needs to be simple in terms of architecture, low in terms of required infrastructure resources, fast in terms of end-user delivery, protected in terms of security, productive in terms of resources accessible, and easy in terms of end-user usability.
The Digital Workplace

What started years ago as application virtualization, transitioned into virtual desktop infrastructure, and eventually landed in what we now call the digital workplace. Simply put, the digital workplace is a consolidated unified portal where users can find everything that she/he needs to fully conduct their work from anywhere using any device under any type of connection. The digital workplace is a mix of virtual applications, virtual desktops, micro-apps, files, SaaS and other needed business resources in a highly contextual format automatically fitted to the user using Machine Learning along with all the enhanced security, continuous authentication, analytics, operations, SSO and other goodies …
For organizations to deliver remote resources in a secure manner and for users to be able to conduct their day-to-day work remotely in an efficient manner, a variation of the digital workplace must be in place. Now we live in a very materialistic world were every vendor manipulates the digital workplace to fit their own agenda, narrative and portfolio of products ( No exceptions here ! ), so the only way forward for organizations nowadays is to deeply assess and understand what constitutes a digital workplace for them subjectively and look for a technology that meets their requirements, needs, and desired outcome.
What resources do my users need to conduct their work remotely, effectively, and efficiently, and how can I deliver these resources in a way that makes my users more productive wile maintaining highest level of security ?
There is NO generally ultimately better solution nor is there an ultimately superior product, it is sincerely all about you as an organization, what solution/product solves your business challenges and achieves your desirable goals which is highly contextual and subjective to you as an organization. A vendor that fails to assess and understand your business as a whole will never be able to claim superiority over any competitor or give generalized statements… !
Evolution of Remote Work
I love community involvement, I really do as its an intrinsic part of my belief system and accordingly I try to help individuals and organizations in achieving their technology goals in whatever space I can provide value. Though I cannot claim I have the resources and/or research that most vendors claim to have and/or have conducted yet I have interacted with many organizations over the last 10 years+ that specifically struggled with EUC encompassing all its variants and meanings. What I have learned over the years is that stakeholders want more productivity which eventually means more profit, administrators want ease of management/support/administration/… and users want a simple, easy, and straightforward way of accessing whatever resources they need to finish their work wherever they are using whatever device they feel more comfortable working with. It is honestly that simple and if any given solution can accommodate the pain-points and desires of these three groups in an organization then look no further.
Users run applications to conduct business and software has become an absolute requirement for almost all organizations regardless of their domain. Application delivery has taken many shapes and forms over the years such as but not limited to: executables, containerized, virtualized, layered, remote, portable, cloud-native and so on … eventually users needed applications to conduct their day-to-day operations and still do. What changed with the boom of cloud technology especially in its SaaS model is the depreciation of Java and the rise of HTML5 which allowed many applications to move from an installable client to simply an HTML5 based browser application. This meant that users do not need to install software anymore and architects need not worry about using different complex technologies to remotely deliver these applications to end users. The more SaaS became popular, the more software vendors moved their applications to HTML5 and now we can see that 99% of software out there are simply running inside a browser.
Of course there are many use-cases that still need standalone applications from the end user side such as graphics intensive applications ( which do run in a browser using a VDI session if needed ) but most organizations out there now rely on SaaS applications to conduct their work, think of Salesforce, Workday, Teams, JIRA, Office365, WebEx and so on …
VDI, in all its different delivery models and sub-technologies and protocols, was the only way to deliver a consistent consolidated secure remote digital workplace to the end user while ensuring centralized administration, security, and control. VDI is expensive, that is not a joke, or at least use to be in terms of CAPEX when done on-premises but with the introduction of the public cloud that is not the case anymore if you decide to use the public cloud. The agility, elasticity, and scalability of the public cloud turned VDI into an OPEX investment rather than a high CAPEX investment in terms of infrastructure needed to host X number of users. So VDI is expensive does not count as a reason not to implement VDI yet architecting, deploying, delivering, and supporting a VDI infrastructure is not a walk in the park and I say this from my personal experience. Many failed VDI deployments and there are a lot out there, was not from the technology, but the lack of understanding that VDI is a change of culture and mentality more than just introducing a new technology on top of wrong sizing, implementation, and assessment of the existing IT environment.
Desktop as a Service (DaaS) on the other hand is still a form of VDI delivery model that moves all the infrastructure/management/support/operations requirements to a service provider that handles all of that for a charge yet there are still a lot of considerations inherited from the technology itself regardless of its delivery model. The most important part is applications that still need to be assessed and planned in terms of compatibility, delivery, and supportability. Think also of the user profiles and data, how is that going to be handled and what needs to be done for it to work such as migration. There is much more to factor in that will need extensive planning hence time to design and deliver correctly which leads me to my assumption that VDI in whatever model it shall be delivered and consumed will require extensive planning and designing thus is not suitable for rashly adoption under critical situations such as a pandemic.
With all the changes we are seeing in technology nowadays and the shifts in trends, VDI is no more the sole technology that enables a digital workplace but still VDI has much more to offer depending on your organizations requirements and context given that the complexity and time-to-market is taken into consideration on top of the steep learning curve for both administrators and users.
With the rise of SaaS and the evolution of HTML5, many organizations can now rely on the web browser to conduct their business. I acknowledge that does not apply to all organizations out there but does to quite a few and I would argue to most. That is all great, but it seems we are back on ground zero, we have been using the web browser for many years now and all of our users have it so what is the catch here ! We still have to publish our resources to the internet opening up our attack surface for users to access resources from anywhere, we still need a browser that can run on any device allowing users to work from their most productive device while maintaining a unified constant experience, we still need to ensure privacy and encryption of stored and in-use data, and we need a browser that enforces our regulatory security controls regardless of the device type and its ownership model.
Zero Trust: Browser Context

I firmly believe in Zero Trust security in its entirety “Assume Everyone is a security threat, Continuously Verify Everyone” but the name provokes me and I have not been able to digest it by any way, shape, or form given the way vendors have been using it. Similar to digital transformation, generalized cliché statements on Zero Trust has varnished its true meaning and shed dark clouds on its essence. First lets start with the name, nothing in life can be categorized by Zero, that is an absolute truth both scientifically and philosophically. Case and point, we trust vendors that deliver our zero trust security so how does that account to Zero !? I am not a pessimist, but people don’t want to think about the ramifications of not inherently trusting vendors and I honestly think they should at least consider the risk. People mitigate this risk by doubling on security components like two different Firewall vendors for example but they do that incase one or the other is exploited not because they are mitigating the actual risk of a security vendor being the security flow. I understand this I really do, if that was not the case , each organization would have to build its own OS, that been said, I believe the right term is “ Minimal Trust “ in my very humble opinion.

I am not going to dive into Zero Trust in its entire meaning as that is a lot to cover and I will do so in an upcoming post called Unified Endpoint Security but for now lets discuss how Zero Trust helps mitigate the web browser security dilemma. As we stand, VDI is no more the sole technology to deliver a digital workplace for many organizations or more precisely, it is a very big technical and operation endeavor to deliver virtual desktops and applications for just securing a published browser. SaaS and HTML5 made the come back for the web browser which can now run many if not most business critical applications from the end-user. This, out of the box traditional browser approach, introduces many security considerations that contradict with the Zero Trust Architecture of not trusting and continuously monitoring users, data, applications, and systems. How can we deliver a secure browser that enables users to connect to intranet resources without having to publish them to the public world, how can we make sure that data at-rest, in-transit, and in-use is encrypted and only accessible to the user, how can we maintain full control over this secure browser that may be used on any device/OS, how can we secure business related data such as files on a device we do not control, how can we ensure that the user will not infect the browser or manipulate it, is the device adequately protected from all kinds of threats even if offline, and can we make sure that this device is compliant with our internal security policies even though we might not control it ?
These tough questions dictated a VDI environment for quite some time because we control the VM that holds the OS and the infrastructure that holds the users, data. and applications thus can maintain compliance and apply all kinds of controls because all resides in our datacenters. The question here is that do we need a VDI environment with all its ecosystem products and considerations to deliver and secure a web browser to access internal applications !?!? Let this resonate for a while.
Even if VDI is a requirement, is it so for all of my workers use-cases or just a specific part but we did not have a viable alternative to go with. Do you want to pay for a full Windows license and all the infrastructure resources needed for a VDI machine just to eventually publish a web browser for a user in order to maintain secure controls !? Remember 10 years ago when we used VDI to deliver IE6 because certain web applications needed it with very specific Java versions and so on !
Realize that the only way you can come up with an answer is after an assessment of your business as a whole and having a solid understanding on what constitutes resources that users need to conduct their work remotely and what technology is needed to deliver these resources. I assure you that many user groups can leverage the native secure browser experience thus saving your organization tons of money while still leveraging VDI for use-cases that actually need and does justify its cost and management overhead.
BlackBerry CylancePersona
Zero Trust is neither a product nor a feature but rather a new security architecture model which entails a lot of considerations, planning, and components. BlackBerry UEM and BlackBerry Desktop do cover a certain part of Zero Trust requirements within the secure browser context but there is much much more to Zero Trust then meets the eye. We realize and acknowledge this fact thus we do not claim we can cover all the Zero Trust requirements for all of your infrastructure (Network Security Micro-Segmentation as an example) but we can definitely do so in the context of users, applications, and data which make the digital workplace.

BlackBerry CylancePersona previously called BlackBerry Intelligent security is a cloud hosted security solution that uses AI/ML/Analytics to continuously assess users, device, application, and data for anomalies in user location, network trust, device/app and user behavior. CylancePersona dynamically adapts a security policy based on user location, device and other factors which can grant/deny access at anytime, issue an authentication challenge, and/or alter/remediate.
The trademark of any Zero Trust model is adaptivity and contextuality since we move the security boundary from zones based (Castle-and-moat) to the combination of different factors that does not care about the user location in a network segment such as internal or external. Factors that are assessed as part of CylancePersona are:
-
User Location: CylancePERSONA uses Machine Learning to identify behavioral and location patterns of multiple users to determine location-based risk. Known work locations can also be preloaded.
-
User Behavior: CylancePERSONA can determine and build a contextual risk score based on learning how and when a user normally accesses data, identifying when the user’s behavior seems consistent and trusted (coming soon).
-
Network Trust: CylancePERSONA determines the frequency of network use and adjusts security dynamically based on that profile. Accessing a public Wi-Fi for the first time would adjust the risk score accordingly.
-
Device/App DNA: CylancePERSONA has the ability to determine whether a device and apps are compliant and up to date, and can adjust the security policy based on the device and app DNA profile (coming soon).
BlackBerry Secure Desktop
I have joined BlackBerry just a couple of months ago and after going through the training of most of our solutions, I can honestly tell you that this is the most technology I am excited about and know for a fact that it is a niche offering to BlackBerry. If you ever read one of my blogs, you know I hate the traditional sales BS coming from any vendor, hence this is by no way a marketing statement, BlackBerry desktop is something truly unique and I have pitched/sold this on my first ever customer engagement with BlackBerry. It just makes absolute sense and fits into the context of what we discussed earlier in terms of an easy, simple, and secure digital remote workplace without all the hassle, complexity, overhead, and considerations of running a VDI environment.
BlackBerry Desktop : BlackBerry Access, Work, CylancePROTECT & Secure Editor
BlackBerry Desktop is a secure containerized chromium web browser custom built and developed using the BlackBerry secure SDK that allows organizations to deliver intranet corporate web and email resources using an end-to-end encrypted channel while maintaining full control over the secure browser container and its corporate content by administrators, supported on all types of devices/OS such as Windows 10, MacOS, Android, and IOS and does not require any type of device enrolment.
Chrome dominates the web browser space with more than 60% of usage and software vendors know that. Most if not all SaaS based applications support chrome and chrome in-itself supports a lots of browser application extensions which makes it really versatile. BlackBerry took the time and effort to invest in building a custom secure SDK for Windows 10 ( and other OS’s but I want to concentrate on Windows ) in order to wrap a custom chromium browser with a security layer that will allow it to create an independent secure encrypted container within the Windows 10 OS which is completely separated from the local OS filesystem and gives administrators full control over that container only regardless of device/OS/ownership/activation/domain/…
The container for this secure browser will prevent leakage of corporate data to personal devices and allow administrators to control what kind of data can or cannot be exchanged from the container which holds intranet resources and the device which contains personal data. The container will be secured by a complex password that is set by the user after installation and activation, thus the container is always fully encrypted until the user opens the secure browser and authenticates with the password.
The container will also allow administrators to lock and or wipe the secure browser and all corporate data that reside in it at anytime regardless of where it is installed. It is unique in the sense that it does not require that your device be activated to any specific MDM solution nor joined to a specific domain or workgroup. All of its features are intrinsic to the application, so when the BlackBerry Desktop secure browser named BlackBerry Access is installed on Windows 10 , it has everything it requires intrinsically to create the container and activate with its administration server ( can be on-premises or cloud ).
BlackBerry Access will also provide end-to-end encrypted connectivity to corporate resources inherently without needing any other components on the endpoint. This means that, if allowed, users can access intranet web resources and email without having to publish these resources to the public Internet and BlackBerry NOC adds an additional layer of protocol encryption which ensures that man-in-the-middle attacks are mitigated. BlackBerry Access includes a fully functional email client embedded within the browser. BlackBerry Access also includes a secure document editor which allows users to download/view/edit documents/attachments from within the container itself to ensure that nothing leaves the secure container and can provide Viewing and annotating of PDF documents.
BlackBerry Access will also support chrome extensions through a policy that is set by the administrator so applications that need extensions to operate such as Office or Zoom can be enabled on BlackBerry Desktop.
BlackBerry also operates a secure NOC which is responsible for routing the traffic between the end points and the corporate infrastructure and that adds an additional layer of security to avoid MITM attacks. Additionally does not require any dedicated public IPs along with NAT/PAT/Inbound ports on the organization infrastructure. This means that you can get up and running with this solution with very minimal resources required. Note also that the infrastructure that supports BlackBerry Desktop is the same one that supports BlackBerry UEM so organizations will also get all the goodies of unified endpoint management for all types of devices. For customers that prefer their data not to pass through our NOC, that is completely supported, with additional considerations such as requiring a dedicated IP/hostname and NAT for the same.
Endpoint Threat Defense
BlackBerry is also introducing Endpoint Threat Defense (ETD) to the BlackBerry Desktop (coming very soon) on Windows 10 and MacOS that is intrinsically built into our SDK which means its part of the Access browser we discussed so no specific agents/clients need to be installed for the same and no new infrastructure components is required, all from within the same unified management console. This desktop Endpoint Threat Defense (ETD) will prevent user targeted threats such as phishing attacks and malicious URL’s using adaptive machine learning sets that can work completely offline. Users clicking on malicious URL’s and/or links embedded into phishing attacks will be directly detected and blocked without any admin or user interference. This is very important when dealing with remote workers because they are located outside of your secured datacenter where you might have APT protection appliances and other security in place which will not apply to those remote workers especially when they are offline or using a personal device. This is huge and will hit production very soon so stay tuned.
CylancePROTECT for BlackBerry Desktop
CylanceProtect for BlackBerry desktop is a comprehensive embedded security component that provides native threat protection, detection, and response to Windows 10 and MacOS using AI/ML (no signatures). Yes, AI is a very big word and I am with you on this, I don’t like to use it often and I am not an expert in the same, I know that ML is a subset of AI so calling it AI is fine technically although I agree with the approach some people take that AI that we have come to visualize is all about singularity and subjectiveness which is still out of reach so lets enjoy ML for now as an available usable subset of AI.
CylanceProtect will come embedded with the installation and activation of BlackBerry Desktop and in that context will provide AI-driven real time protection from viruses, malware, memory exploitation, scripts, rogue applications, and zero-day threats to the full endpoint. The power of CylancePROTECT is that it works to detect and stop malware prior to execution using a large set of ML acquired data sets unlike most traditional AV products out there that use signatures to detect malware after execution. More so, because CylancePROTECT was built and operates purely using AI/ML, updates are rarely needed and can operate completely offline even detecting zero-day attacks.
In the context of BlackBerry Desktop, CylancePROTECT will be used to protect files moving from the secure BlackBerry desktop container to the local OS and vice-versa (if administrators allow the same via policy). This ensures that remote workers accessing and interacting with corporate resources via BlackBerry Access aka. BlackBerry Desktop will not be able to infect or put these corporate resources at risk regardless of the security status of their device. Coming in the future, BlackBerry CylancePROTECT will also be able to protect files within the secure container which will be something only BlackBerry can do since it owns the secure SDK for the browser.
If Coronavirus was a Cyber Threat, CylancePROTECT would have proactively prevented it.
BlackBerry Digital Workplace
I have stated that not all use-cases can be accommodated with simply a browser, an example is graphic intensive applications or legacy in-house applications that still use a hard-coded client application. BlackBerry Desktop natively integrates with Awingu which does exactly that, deliver virtual desktops and applications through a browser directly inside BlackBerry Desktop aka. BlackBerry Access Secure Browser. Awingu utilizes Microsoft Remote Desktop Services to facilitate delivering virtual apps and desktops via RDP encapsulated for HTML5 and can be opened from within Access through a shortcut embedded into the browser for very easy accessibility and use. The same considerations for different VDI solutions apply such as required back-end infrastructure resources to host the servers delivering sessions that being desktop or application plus RDS CAL’s and others. BlackBerry desktop with Awingu native integration is called the BlackBerry Digital Workplace and this would cover the requirements of most organizations out there.
Althoug this whole post is directed towards a fast, secure, and easy alternative to providing remote access for workers without requiring a complex VDI solution or an Anti Zero Trust VPN solution, I will provide some guidance on the design/sizing/deployment requirements for Awingu since its not a VDI solution per se but more of a gateway that is integrated with BlackBerry secure browser providing a native experience (more on that in the architecture part). The reason is simple, as stated earlier, not all applications run in a browser hence a virtual delivery method must be in place to support workers that need these applications to conduct their day-to-day business. Awingu also adds value in terms of user files access/management if all of your file servers are still on-premises and not SaaS stored/accessed. Last but not least, Awingu integrated portal within BlackBerry Desktop can act as a unified store to even publish shortcuts of SaaS URLs that will open within BlackBerry Desktop making the end-user experience easier.
Worth mentioning that Awingu with BlackBerry Desktop can also offer native browser based secure RDP remote access to existing workers laptops/desktops on top of secure access to existing CIFS SMB shares. Publishing RDP directly is the worst thing you can do so please don’t under any circumstances. Awingu can act as a secure broker while BlackBerry Desktop can act as a secure container to provide secure remote access to your desktop that is sitting in your office.
Dont Panic, Never Ever Publish RDP.
BlackBerry UEM

BlackBerry Desktop is part of BlackBerry UEM and although BlackBerry Desktop does not require any type of UEM enrolment on devices to function yet organizations will get all the goodies and features of UEM out of the box available for use with mobiles and desktops if needed using the same infrastructure and the same console so a unified experience for users and administrators. UEM for desktops that being Windows 10 and MacOS can be used to enforce different security policies such as device policies and more importantly compliance policies for BlackBerry Desktop. Administrators can make sure that user devices are compliant with their baseline security policy before being allowed for example to open and work in BlackBerry Desktop.

Many UEM security policies exist and are being added for Windows 10, and I for one am looking to a time when all group policies with no exceptions can be applied through UEM and we get modern management the features it deserves.
What About Mobile Devices !?
Seriously read this carefully, we are the only vendor out there that can give you email and intranet access to corporate resources with a consistent experience as the one we are discussing on your thick clients that being laptops or desktops or otherwise with exactly the same infrastructure but more importantly, you don’t need to enroll your device or install any agents. Our custom email and web applications for mobile, same as BlackBerry Desktop, have all the required parts intrinsically to operate without any enrollment or agent so your users can just install for example BlackBerry Access secure browser or BlackBerry Work secure email client and directly start working, all using a very simple email with an activation key !!!

BlackBerry is the only vendor in the market, at least to my knowledge, that provides the ability to secure applications by means of containerization and remote access that being proprietary, ISV, and/or in-built SDK wrapped without the need to install any UEM client and/or Enroll the endpoint/device to an UEM infrastructure.
Essentially users can just install BlackBerry Access for example (A custom-built security driven chromium browser) and access internal web resources (without the need to publish these resources online) securely without having to install any special agent or go through lengthy MDM/MAM enrollment procedures. Same goes for ISV and custom in-built applications by customers that can be wrapped with BlackBerry SDK.
Users receive an auto-generated email ( linked to AD attribute ) with an access code that is generated by the administrator and that access code is used to authorize the application which is then completely containerized and securely remotely accessible with administrators having full control over that specific application and its data in case wipe or lock is required at any time.
Administrators that being infrastructure, networking, and security on the other hand have an easier time providing secure access to internal resources with full AD integration and without having the end user risk their domain password on endpoints (given how long and complex they have become !) on top of not having to publish internal web resources online with the ability to control business related apps settings and data at anytime.
BlackBerry Desktop User Onboarding
Onboarding users is as simple as its get even for Tech-Savvy end-users. Administrators can automate onboarding of users via domain groups or user lists in which they receive an email with an activation code for the same. Users just have to open their Access browser and enter their email and activation code. That’s it, now users have access to all their “authorized” intranet resources such as web applications and email on top of an embedded secure file editor for handling files/attachments within the secure container, all in a native browser experience that users already have experience in and are comfortable with.
BlackBerry Desktop Infrastructure
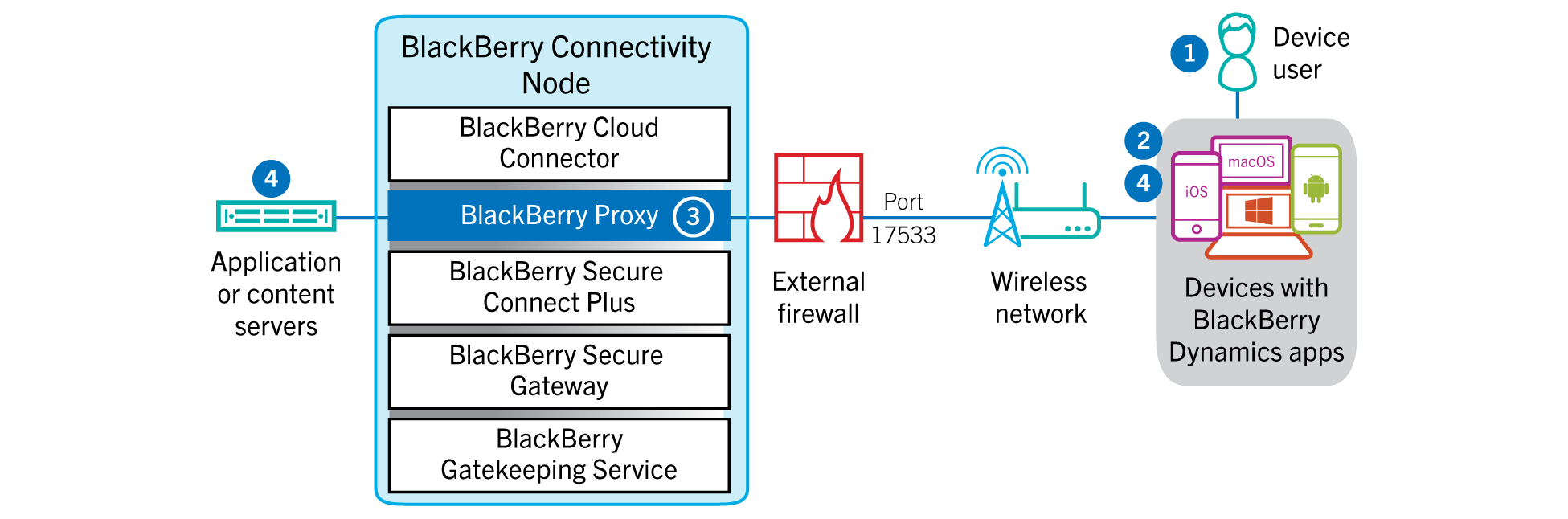
BlackBerry UEM – Cloud
To make a legit specific statement on deploying BlackBerry Desktop, I can say that if network and infrastructure prerequisites are in-place, you can get up and running production ready in 30 minutes. Prerequisites for BlackBerry hosted cloud UEM instance to support BlackBerry desktop using our NOC is very minimal, we just need two virtual machines ( Server 16/19 , 4 vCPU , 12GB RAM , 80GB Available Disk ) that have outbound internet connectivity directly or via a web proxy along with a service account to hook into AD/DB/Off365/Exchange. These VMs called BlackBerry Connectivity Nodes will need port access to internal resources that users will access such as web applications and email. That’s about it and your users are set for working remotely in a secure manner using a native browser experience since our NOC will handle securing and routing the traffic through Direct Connect can be used with Cloud UEM as well with the requirement of one public IP and one public hostname NATed to the UEM BCN nodes deployed in DMZ.
BlackBerry UEM – On-Premises
Prerequisites for BlackBerry on-premises hosted UEM instance to support BlackBerry Desktop without using our NOC is (at minimum because we can split UEM BCN, Core, and BEMS for security purposes as depicted below in the drawing and the same sizing can be used for th rest of the machines if you decide to split them) two virtual machines ( Server 16/19 , 4 vCPU , 16GB RAM , 80GB Available Disk ) that have outbound internet connectivity directly or via a web proxy along with a service account to hook into AD/DB/Off365/Exchange. These VMS will host core/mgmt./BCN/BEMS components and will need port access to internal resources that users will access such as web applications and email. Because our NOC is not being used, we need one public IP that will NAT only one port alongside a public FQDN for the same. CylanceProtect hybrid appliances would also need to be added if threat protection is required knowing that this is only a management console that includes no traffic so the proffered model is to keep it on the cloud, soon enough we will integrate CylanceProtect management into the UEM console.
The easiest way to tackle port and internet requirements is placing these 2 virtual machines in the DMZ and opening ports to internal required resources such as AD for LDAPS, Exchange for SMTP, and SQL for DB on top of any resource that remote users need to access such as web servers. Another approach if you have an ADC is just load balancing / SSL offloading these components on your ADC and deploying these two VMs internally to avoid opening ports from the DMZ to your internal resources then use web proxy for required outbound internet traffic.
If direct connect is to be used ( fully on-premises with traffic not routed through BlackBerry NOC ) then one public IP is required to NAT a single port to the load balanced IP of those 2 blackberry UEM VMs.
BlackBerry Digital Workplace
BlackBerry Digital Workplace is BlackBerry Desktop with the addition of Awingu as a virtual gateway. Awingu is not a VDI product per se, it exists for the purpose of simplifying VDI deployments by leveraging Microsoft RDS for session based remote desktops and applications and does so by wrapping them for delivery via HTML5 utilizing RDP protocol. Awingu can do a lot more as well, aside from virtual desktop session and applications native browser delivery, it can act as a reverse proxy for web resources (when used within BlackBerry Desktop that is not required since BlackBerry is doing the secure reverse proxy functionality with all the added security) on top of providing easy browser based access to files and folders all from within a single unified console with added MFA security if required. In the context of BlackBerry Desktop, Awingu can be used to publish URL shortcuts for all intranet resources that will be securely accesible via BlackBerry Access browser thus makin the end-user experience simpler.

On top of the UEM requirements discussed in earlier sections, Awingu will require two virtual machines for its own services. Now sizing Awingu and RDSH servers is going to be tricky because there are a lot of variables to consider, especially applications and network (RDP even HTML5 wrapped does eat a big chunck of Kbps). Aside from that, we need two virtual machines for RDS connection broker (only required if publishing remote apps because of internal RDS permissions requirements). We will also need two virtual machines to act as file servers for users profiles/data, or existing file servers can be used. The number of Remote Desktop Session Host (RDSH) servers will depend on the number of users and applications that users will utilize. I will give you a baseline sizing but that is just a very general starting point that needs to be assessed and tested.
- Awingu Appliances: As per Awingu documentation, the number of appliances depends on the RDP streams that every user will need such as multiple apps opened on the same RDSH server or on different RDSH servers. Add more Awingu appliances in a multi-instance setup as needed.

- RDS Connection Brokers: I would recommend 2 x 4 vCPU and 12GB RAM Server 2019 VMs.
- RDSH Servers: This will highly depend on the number of users and what kind of applications are being used. As a baseline for users that will work with Microsoft Office and standard applications: 8 vCPU and 40GB RAM for 25 users on a Server 2019 RDSH server.
- Bandwidth highly depends on the applications that are going to run. For applications without audio/video/graphics I can assume around 150 Kbps per user while with audio/video 300 Kbps while with intensive graphics around 450 Kbps.
- Profiles/Data wise I would size 1GB per user for a consistent profile (FSLogix) and XGB for how much the user is allowed to save data in the back-end datacenter. Data could also be a central location or cloud drive that the user works with so no need to add any storage for that but at least pure profile storage is required to maintain configuration between different session host servers. In session based application/desktop delivery environments, I don’t recommend FSLogix for data as well, just the profile, either connect to existing shared drives or cloud drives to work with business data or use folder redirection for the same.
Again all are just baseline standard recommendations and should be customized to fit the environment, users, and applications. Also note that for secure browser RDP access to existing desktops, only the Awingu appliances are needed while other components are for session-based VDI requirements.
Cloud Competitor FUD
The reason we need outbound internet connectivity even with an on-premises deployment with direct connect is that we perform activation and push policies to devices using the BlackBerry infrastructure which does not store any customer traffic, just like how APNS is needed when activating IOS devices, we have the same approach to confirm user licenses, identity, and connection. This infrastructure is present in most countries locally so complies with all government regulatory bodies and a very big advantage here is that we don’t need an additional public IP/hostname for only activation of devices which is a very big waste nor do we need all the additional ports and firewall security rules to facilitate the same.

Unfortunately many competitors have spread FUD on this point claiming that we are only cloud based which is completely untrue, the BlackBerry infrastructure is only used for activation, licensing compliance and policy management which does not store any customer related traffic exactly the same as Apple forces APNS connectivity requirement for activating IOS devices which is mandatory so for those vendors I would say if you can remove the requirement of activating IOS with outbound internet connectivity to APNS then we can happily facilitate the same, knowing that Apple operates its APNS servers in the US while we have a local infrastructure in almost all counties such as KSA and UAE in MEA. The BlackBerry NOC is yes a cloud based operations center that would interfere in customer traffic although its fully encrypted and only customer’s UEM can decrypt that traffic ( we have very high security sensitive customer running on this … ) but for the sake of argument, this is completely bypassable with Direct Connect which uses the customer own datacenter components to facilitate traffic routing between end users and the UEM environment.
BlackBerry Desktop Deployment Time
I can make a legit generalized statement that you can get up and running with BlackBerry Desktop in 30 minutes or so without even blinking. The statement is true to me but will definitely not be true to you as an organization. The actual work needed to get up and running is more of covering the prerequisites and requirements on your environment rather than what needs to be done from BlackBerry side so its highly contextual. On-premises or cloud hosted, you can have BlackBerry Desktop functionality up and running using a single VM for up to 5000 users but surely organizations want HA at least and may have different security practices dictating the separation of components and so on ..
I have seen statements made that organizations can spin up a VDI environment in matter of minutes or hours. That is absolutely absurd, is not realistic, and pure marketing nonsense. VPN, yes of course, but then again VPN is the anti Zero Trust and I honestly believe its time to let it go as it has out served its purpose by years …
Licensing
I will let marketing worry about the kind of support BlackBerry is officially offering in response to the current pandemic with Coronavirus, never the less I can confidently state that we can offer 30 days trial ( more if you count the grace period ) of BlackBerry Desktop with no strings attached. Its easy , straightforward, requires very low resources, and serves a very specific purpose. If what is discussed earlier applies to you as an organization then feel free to directly request a trial license and follow the deployment procedure below.
This blog is my way personally and as part of the sales engineering team at BlackBerry to give back during a time of crisis. Even if you need to renew the license for some additional time, we can facilitate that again with no strings attached. Feel free to reach out to me if you have any issues with the below or your respective BlackBerry team in your region, we have a very supportive team that loves the community.
Worth mentioning that BlackBerry Desktop is part of all BlackBerry UEM suites. CylanceProtect and Secure Document Editor are Add-ons to the suite and priced in a very attractive bundled package. Adding Awingu to the mix for any application that cannot be delivered via the browser natively, we have an end-to-end offering names BlackBerry Digital Workplace which includes all the for-mentioned components in a single licensed offering.
Deployment
I am going to deploy BlackBerry UEM On-Premises with Direct Connect (MEA region is set on having data not pass through any cloud component) delivering BlackBerry Secure Desktop. I will use a single VM to host all UEM components such as Core, Management, and BCN (BlackBerry Connectivity Node) situated in DMZ and will open access for users to intranet and email corporate resources. Depending on your environment, you might want to add more servers for HA and to accommodate a very high number of users on top of splitting components on different servers but for the sake of this demo, I will install all components on a single server.
BlackBerry Desktop
Step 1: Signup for a BlackBerry UEM Freedom Suite trial which grants you a BlackBerry MyAccount. Download BlackBerry UEM software and create an On-premises UEM server in BlackBerry MyAccount. (5 minutes)
Navigate to https://www.blackberry.com/uk/en/products/blackberry-secure-uem-suites and choose TRY under Freedom Suite.
Enter the required information and click on the link that is received in your business email after which an BlackBerry My Account is created.
Login to your BlackBerry My Account to verify account is activated and proceed to step 2.
Navigate to Server Software Download and download BlackBerry UEM. BEMS ( provides Lync,Skype,Jabber integration and email push notification services ) and other components may be required if you are looking for a full UEM platform for mobiles and desktops but for now we are looking at BlackBerry Desktop which only required BlackBerry UEM.
Create an On-premises UEM server which will produce an SRPID and AuthKey that will be used later to activate the UEM server to its designated account.
Step 2: Prepare a read-only domain service account with local administration permissions on the UEM VM and create an inbox if SMTP integration is required or user another user for the same. (5 minutes)
Run the following on the exchange server from the Exchange Management Shell to support mail push notification service through BEMS incase required in the future. You can change the name of the role assignment.
New-ManagementRoleAssignment -Name:BlackBerryAppImpersonation -Role:ApplicationImpersonation -User: ServiceAccount
Step 3: If SQL express is to be used then nothing is required other than a direct install of SQL express ( will be automatically done by UEM installation) but if an enterprise SQL is used then add the service account temporary to dbcreator until the DB is created then remove it after installation and set service account on created DB to dbowner. I will use an SQL express installed on the UEM node. (5 minutes)
Step 4: Verify the VM that will host UEM software has the required prerequisite components such as Java. (10 minutes)
First make sure that the service account is added as a local admin on the BlackBerry UEM node and given the login as a service permission via domain or local group policy. After that has been done, logout and login with the service account to continue installation of BlackBerry UEM.
Install JAVA JRE 8 runtime on the machine and create a Windows environment system variable for the same.
Step 5: Open the required network ports and configure the required NAT pointing to the UEM VM. (No Way I can Determine that for you, too many variables to consider but if your network/security team are in a good mood, its a walk in the park)
BlackBerry UEM nodes should have internet connectivity to the following public IP addresses for only two ports (The following is for BlackBerry Infrastructure in MEA for KSA and UAE) while all others can be found at https://support.blackberry.com/community/s/article/36470 . This can be direct internet connectivity or through a web proxy out-bound initiated.
Also 443 out-bound initiated should be allowed to the following BlackBerry hosted services for application policy delivery and push services. Can also be opened using a web proxy:
-
206.124.114.1 to 206.124.114.254 (206.124.114.0/24) on port 443
-
206.124.121.1 to 206.124.121.254 (206.124.121.0/24) on port 443
-
206.124.122.1 to 206.124.122.254 (206.124.122.0/24) on port 443
Since this will use Direct Connect which does not use BlackBerry NOC because of regulatory considerations especially in MEA, the following options can be configured for the same: 17533 need to be Nated and a public hostname needs to be created pointing to the public IP that will be used to NAT/PAT.
-
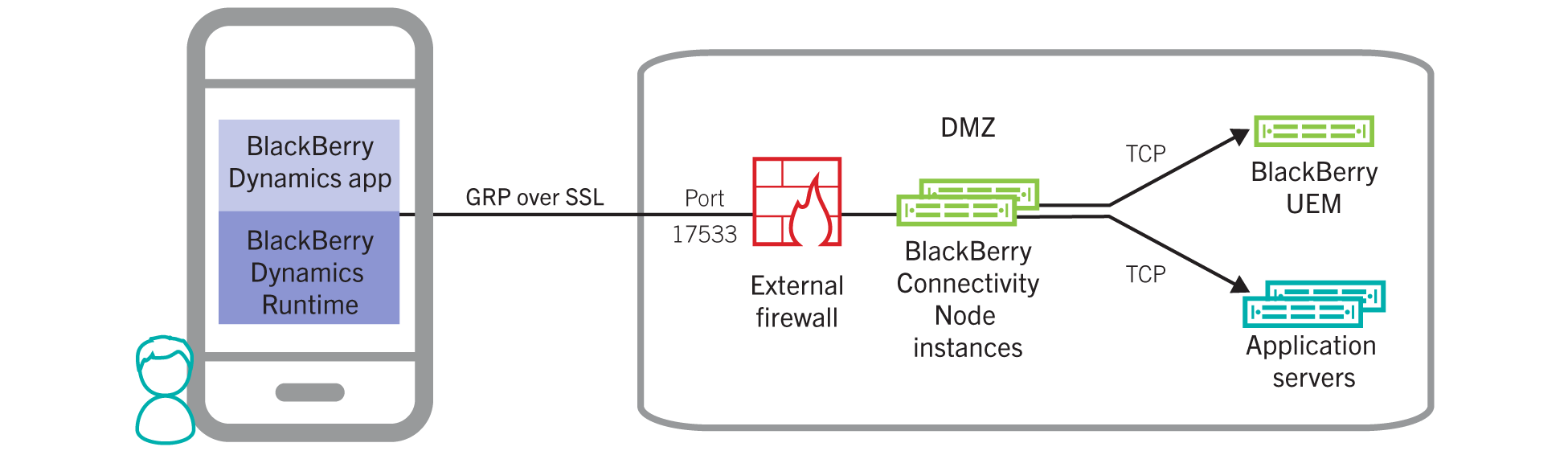
Port Forwarding: You can port forward all incoming client traffic to a BlackBerry Proxy server in a DMZ. The benefit of this approach compared to the other deployment options is that no extra appliance required in the DMZ. Port forward (NAT/PAT) port 17533 to the BlackBerry UEM node.
-
Reverse Proxy: Use reverse proxy for server-side load balancing using your own scheme, instead of a round robin scheme using DNS. In addition, using a reverse proxy with SSL bridging allows you to authenticate BlackBerry Dynamics apps in the DMZ using client certificates issued by your own certificate authority. You can set up Direct Connect with a reverse proxy server using an appliance like F5 BIG-IP Local Traffic Manager (LTM) or Citrix NetScaler. Port forward (NAT/PAT) port 17533 to the LB IP for the UEM nodes on NetScaler or F5.
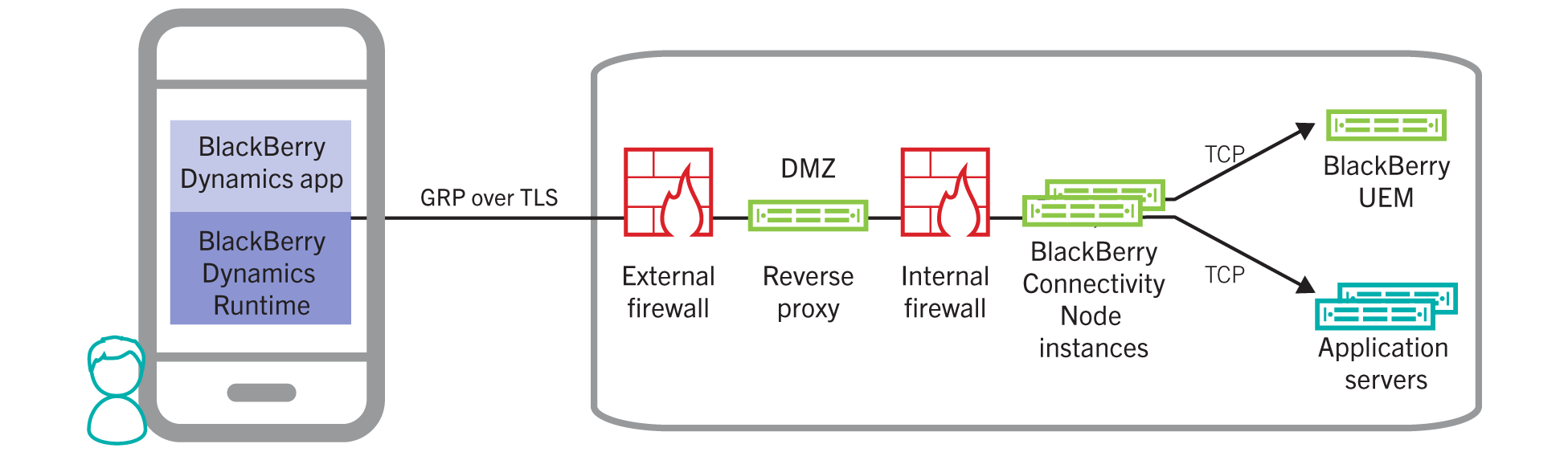
Finally open AD/Exchange/Web ports from the UEM node hosted in the DMZ to these resources. LDAPS TCP 636 for AD, 443 TCP for Exchange and probably 443 to your intranet web resources that users need to access remotely.
I have simply created a PAT from one of the public IPs to the UEM node for port 17533 plus create a public hostname record pointing to that public IP from my domain registrar. I also added a PAT for port 443 to enable user self-service but that is not mandatory.
Step 6: Install UEM software with all components. Open web console and activate the UEM server. (20 minutes)
In regards to VM sizing for UEM node, it depends on the components its hosting but generally here is a summary of what is required when all components are consolidated on the same VM:
-
Up to 2000 users:
-
Up to 5000 users:
-
Up to 25,000 users ( per node ):
Run the BlackBerry UEM Readiness Node to verify that all prerequisites are met. If using a proxy, make sure to choose that option and point to the proxy being used.
Now lets run the BlackBerry UEM installation. I am installing all the roles on a single node but depending on the deployment architecture required this can drastically change yet the prerequisites are the same.
Login with username: admin and password: password for the first time via https://localhost/admin:443 then enter the server registration details collected earlier when the on-premises server was added to the BlackBerry MyAccount. Also set a new user for the admin default account.
Step 7: Configure Dynamics connectivity, password, and container policies. (15 minutes)
First lets start by configuring Direct Connect which prerequisites were already configured earlier in terms of a public hostname and public IP address with NAT/PAT.
A proxy server can be used for outbound-initiated traffic for the BlackBerry Server, BlackBerry NOC, and BlackBerry Proxy.
-
BlackBerry NOC Traffic
-
BlackBerry Proxy Traffic
-
BlackBerry Server Traffic
Next we need to configure the BlackBerry Dynamics policy which will dictate the container password settings for BlackBerry Desktop. Here we can enforce complex passwords for users to access the BlackBerry Access container on desktop machines or even go with passwordless.
Now we need to configure the Dynamics Connectivity profile which states what will be routed directly when the user uses BlackBerry Desktop such as google.com and/or what will be routed internally such as intranet resources that users are allowed to access. The FQDN of your email and intranet resources should be added here.
I will choose to route all traffic through BlackBerry infrastructure which means that when users use BlackBerry Access browser aka. BlackBerry Desktop, all traffic within that being email and intranet will be routed through our environment.
Default domain augments any entered name in BlackBerry Access with the domain name specified here. For example, if a user enters http://emailserver , BlackBerry Access will amend it to access http://emailserver.defaultdomain.com .
Inside additional servers, add any intranet resource that users will need access to with the required port such as Exchange OWA, SharePoint, and any other web application. You can also add an IP range which will allow access to all servers with IP addresses in that range.
Step 8: Configure BlackBerry Access (Desktop) policies and user email settings. (10 minutes)
There are a lot of policies that can be configured, I will only touch base on things that need to be configured for email to other options like setting a default search engine and allowing third-party extensions.
One important setting here is Enable export of downloaded files to OS file system which enables or disables moving files between the secure container and between the local OS.
Step 9: Add AD groups/users with auto-enrolment. Users will receive an email with the procedure to activate BlackBerry Access. (5 minutes)
First lets add the domain to BlackBerry UEM and then sync a group of users to assign the policies create above and auto-enroll them into BlackBerry Desktop. Users will receive an email with an activation code for their BlackBerry Desktop ( Access ) after that.
Now that AD groups configured have been synced, we add them to the UEM groups and assign the previously created Dynamics policies to this group plus the entitled applications and associated services. For BlackBerry Desktop that would be BlackBerry Access as an application and secure editor as an service entitlement ( I don’t have the entitlement in my trial but can be requested for yours ).
You can change the template email that users will receive when they are added to the groups synced in the above mentioned configuration. Every 5 minutes, UEM will sync with AD and check for any new users added to the synced groups, enroll them, and send an activation email, all automated. Offboarding is also automatically configured so that if a user is removed from all synced AD groups, BlackBerry Desktop secure container will be wiped from the device.
For BlackBerry Desktop, I create a new template that directs the user to downloading, installing, and activating BlackBerry Access which should not take more than 5 minutes tops and is as easy as click next couple of times and copy the activation code.
Step 10: Test !
Users will receive a custom email as per the template created above instructing them to install and activate BlackBerry Access. All other information needed such as mail server or default home page are pushed by policy. Users will have to enter their AD password only once when opening Access native HTML5 mail client for the first time and even that can be avoided by configuring KCD SSO.
Download the BlackBerry Access installation file from here and install ( add these to the custom email template ). Installation is simply two-next clicks …
This password will be used to open the secure BlackBerry Desktop Access container by the end-user at every launch of the BlackBerry Access application on desktop.
That is it and now users can access intranet resources that being web, email and/or Awingu based virtual desktops and applications via an embedded shortcut. As I was taking a picture of the same, seems that I did not allow screenshots via the dynamics policy so whenever a screenshot was attempted, this was the result.
Cool, lets enable screenshots for the sake of this blog in the Dynamics Container Policy.
Directly on the spot, the policy applied and I am able to take screenshots from within my secure BlackBerry Desktop. This is accessing a non-published internal IIS server via a private IP. Opened OWA as well.
Now lets open the embedded HTML5 fully functional email client for those that do not like OWA. Here we have email, calendar, and contacts.
Okay so we have some applications or desktops that can only be delivered via VDI, Awingu to the rescue running a virtual session inside our secure browser, all with just a click on a link.
That is not all ,we still have the embedded secure editor, CylanceProtect, and many UEM policies that can be applied even without enrolling this Windows 10 machine to the MDM server and more so it doesn’t care on what network we reside or what domain the machine is joined. The security is embedded into the BlackBerry Desktop browser and that is all that matters.
An example of an UEM driven policy that applies to BlackBerry Desktop and is of the utmost importance is compliance and full container control. We have tons of compliance rules that can alert and take action as well. Here is an example:
Even with this being just an activated application with no special agent or MDM enrollment, we have the option to delete work data, remove device, and temporary lock the BlackBerry Desktop at anytime with instant effect. More so, a compliance violation is present which relates to the antivirus, that is because I configured a compliance policy to alert the administrator and the end-user that our corporate approved AV is not in place and to continue operating BlackBerry Desktop you have to fix the same else action is going to be taken to lock and/or delete the container.
I am not going to cover the CylanceProtect part because I don’t have the BlackBerry Desktop unified installer in hand as of now that includes the CylanceProtect component but that is also simple and straight forward in terms of installation, activation, and policy management. I will cover the same very soon in a future blog.
BlackBerry Digital Workplace ( Awingu )
For the sake of this POC, we are going to deploy a single Awingu appliance situated in the internal network ( since BlackBerry Desktop is handling the external connectivity part ). This appliance will have standard LDAPS access to AD, SMB access to user CIFS repositories, and RDP access to RDS servers and existing desktop/laptop devices. This appliance will utilize its existing internal DB since its a POC ( under 200 users ) and a trial license which will only work for 2 concurrent sessions ( this is not realistic for a decent trial/pilot so contact us and/or Awingu to get a license for more number of users and sessions ).
Microsoft RDS is needed if access to virtual session desktops and/or applications is required so for a POC we just need a single Microsoft Server 2016/2019 with RDS services Broker and Session Host installed. This server will have all the required applications installed locally and published to users as virtual applications. Now if you are looking for a production environment, you can setup a full highly available RDS environment using this post Deploy Microsoft RDS 2019 HA with Azure DB and VMware NSX Load Balancing. An RDS server is not required if Awingu is being used to provide secure browser based RDP access to existing machines and/or secure browser access to existing SMB/CIFS repositories.
Step 1: Download and Import Awingu virtual appliance. Choose the Free Pilot version to get access to the downloaded virtual appliance. DHCP is default and can be changed manually through the console after the appliance OVA has been imported successfully.



Step 2: Connect to the appliance via http://ip:8080 and finalize its configuration by setting the local admin password, specify the database, and specifying the DNS/NTP settings. Make sure to create an A record for the appliance on the internal DNS server.







Step 3: After the installation is completed successfully, time to setup the AD/LDAP(s) connection and Awingu certificate then add the AD groups that will be given access to resources.



Navigate to System Settings then verify license via Global – General Info.

Navigate to Global – Domains . Click on ADD to configure AD/LDAP integration. If you have a cert on your AD then secure LDAP is supported so use it ( An update is going to be pushed by Microsoft in June or so that will stop standard LDAP 389 from working so secure LDAP is a must ).





Navigate to Global – Certificates tol import a trusted certificate for Awingu so that users are not prompted for an untrusted SSL connection when trying to access the same. Since this is a linux appliance then the standard windows pfx cannot be used rather we need the pem cert and the security key of the certificate. This could be a wildcard cert or an single FQDN cert using Awingu hostname. If you have an pfx and want to export the pem cert and key then use the following procedure:
-
Open CMD and run the following command:
set OPENSSL_CONF=c:\OpenSSL-Win32\bin\cnf\openssl.cnf -
Copy the pfx cert into the the folder C:\OpenSSL-Win32\bin
-
CMD to C:\OpenSSL-Win32\bin
-
openssl pkcs12 -in wildcard.pfx -nocerts -out key.pem –nodes
-
openssl pkcs12 -in C:\OpenSSL-Win32\bin\wildcard.pfx -nocerts -out key.pem –nodes
-
openssl pkcs12 -in C:\OpenSSL-Win32\bin\wildcard.pfx -nokeys -out cert.pem
-
openssl rsa -in key.pem -out server.key
-
cert.pem is your certificate and server.key is your private key ( without a passphrase )


Navigate to Manage – Labels to add the AD groups as labels which will later be assigned to virtual apps/desktops for resource access.




Optional: Navigate to Configure – User Connector and add the label Domain Admins and Domain Users to Login Permissions so only users of those groups can login to Awingu ( this is different than resource assignment ).


Step 4: Assuming you have an RDS server with all applications required by users installed and that has the Connection Broker and Session Host roles added, time to add the same as an application server in Awingu, publish required applications/desktops, then assign to domain users for accesibility. Navigate to Manage – Application Servers.

Choose Import from AD and add the RDS server or servers.

The number of max connections would be determined by the sizing conducted in terms of applications that are going to be used by the user but for a POC my recommendation would be max of 25 users. The server Label will be created automatically but if this was a connection broker published app/desktop in a production environment, you need to manually add the server label as rdscollection.<collection name> then the broker will handle the session assignment and load.

Navigate to Manage – Applications.

First we will publish a desktop session (Desktop Application) for users which means users will get a full desktop to work in which will be hosted on an RDS SH server in the backend datacenter.

Under Servers, choose the labels ( auto created with server name when application server was added ). All servers added here will host desktop sessions.

Now for Remote Applications, first they need to be added on the connection broker then the Alias present here will act as the application published name on Awingu.


Now that we have our published applications and desktops ready to go. Lets provide users with secure access to their SMB shares. This is very important in the secure browser context because these files will always open within the secure container ( unless specified otherwised by policy ). This is another reason I recommend folder redirection for Data ( Desktop, Documents ) because we can publish the user profile data as external shares present in Awingu so they can be downloaded then sent by BlackBerry Secure Desktop embedded email client and/or edited by our Secure Document Editor then uploaded again to the user data share. Vica-Versa this would allow users to download attachements securely inside the browser container then upload them to the user data repositry all from within the browser with no interaction with local OS for security purposes.
So for VDI and/or application virtualization here I would recommend FSLogix for the user profile and folder redirection for the user data ( user profile is customization, start menu, task bar, appdata, registry … while user data is desktop, documents, downloads … ). Apply Folder Redirection to OU that hosts RDS/VDI servers/desktops with loopback processing enabled since its a userp policy and point it to the share created for user data. This will create a folder for every user once they login for the first time, then this folder can be published to the user as a CIFs share so they can work with these files/folders from within the VDI/App sessions or diretly within the secure browser (which BlackBerry Access cannot do on its own, I mean access to SMB shares). Also note that FSLogix for shared desktop/app sessions does not support multi-write applications which is okay for profile, SaaS, and Client-Server apps but not for data and multi-write applications but folder redirection does ( last write wins ).
Now lets navigate to Manage – Drives.

I will add a CIFS share that will point to the user data via the <username> variable so if your folder redirection policy points to //fileserver/data then your user will have their data saved by the policy in //fileserver/data/username so we use that variable for automating this for all users.


Another add value of Awingu in the context of BlackBerry Desktop is the ability to publish web resources as shortcuts that will be opened inside BlackBerry Access directly. This will make the end-user experience simpler as all of their web shortcuts will also be visible from the Awingu page which can be branded and customized. Because this is being used within BlackBerry Access, we dont need to use the Awingu reverse proxy since our secure browser is already doing that.


Last we will configure BlackBerry Desktop aka. BlackBerry Access to auto-configure the built-in Awingu integration by specifying the Awingu server it needs to connect to.




Step 5: Testing wise I would recommend first tesing internally using a standard chrome browser then after all functionality has been tested move on to BlackBerry Desktop aka. Access .








Conclusion
VDI is not dead nor is it a legacy technology but it is way too complex to be adopted in severe situations and under extreme circumstances. Cloud may have mitigated CAPEX cost of VDI and DaaS may have eased up complexity of deploying VDI, yet in itself, VDI as a technology is still a very big undertaking for organizations both technically and culturally.
That been said, and under normal circumstances, I would advise everyone to adopt VDI in one or all its forms. The added value of the technology as a whole is nowadays unprecedented and a real core business enabler for most organizations. With the right planning, design, sizing, deployment, and cultural change, VDI is a dream come true.
Users are now able to conduct most of their work using a web browser, they are accustomed to the browser experience and want to access it from their preferred device working from their desired location securely . Organizations, in order to maintain and advance productivity, need to provide users with an easy and secure platform that provides them with all the resources they need to be productive regardless of location, device, and situation.
Considering the Coronavirus worldwide pandemic, organizations can get BlackBerry Desktop and BlackBerry Digital Workplace up and running in no time with very minimal resources to support users working remotely from their preferred location using their preferred device in a secure manner using a native browser experience with minimal infrastructure requirements while maintaining a very high level of productivity and security.




















































































































Dear SAADALLAH,
Super impressive of what you have done here, providing a step-by-step setup example.
Just thinking from a SMB point of view, if they don\’t have someone like you working for them. The BlackBerry Zero Trust Digital Workplace is useless for them!
How about this?
There are lots of SMBs that have nothing setup and want to get started from ground zero (does not have a corporate email, just using Gmail, WhatsApp, Messengers, Skype and Microsoft 360), but now want to get secured online protection for their small business, after seeing all the ransomware, or want to have their employees work at home during the COVID19.
How could you help these millions of SMBs around the world?
\”Zero Trust Digital Workplace-As-A-Service\”?
Imagine a few (3) most common and make sense setups for a typical no-clue SMB which has no \”on-prem\” equipment.
BlackBerry hosts all the necessary servers for email and all other services required, on one of the clouds (BlackBerry, Azure, Google or Amazon).
These simple SMBs, just need to sign up to the \”Zero Trust Digital Workplace-as-a-service\” with their account number and passwords etc.
Then, press one button, all are setup for them to that pre-configured setup, and they are off and running.
With this, you can truly bring the SMB from a ZERO to a HERO!
Cheers.
Interesting thoughts there , worth considering , thanks for the comment .